The SafeInspect platform is a domestic solution for effective control over privileged accounts and sessions in modern information systems, both classic and cloud. The solution has a wide range of functionality, effectively delimits access to different levels of resources, allows being integrated into any existing enterprise infrastructure, and minimizes the risks of information disclosure.
How the SafeInspect solution works
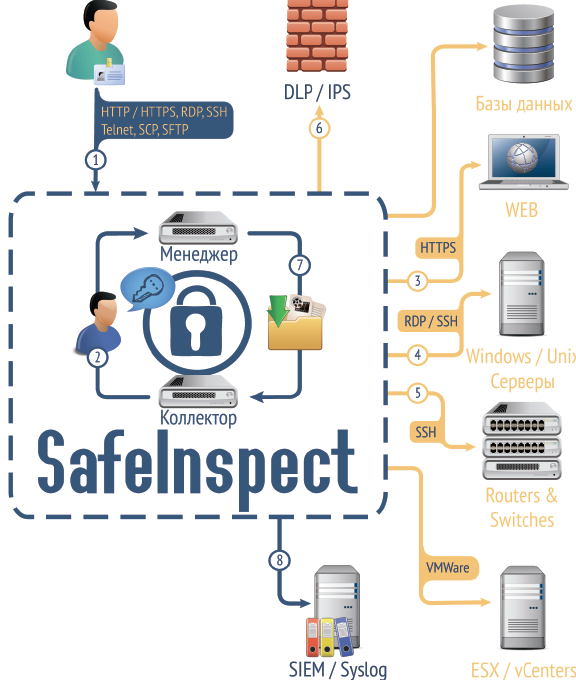
1. Connection
2. Authentication and authorization
3–5. Connection to resources
6. Sending data to DLP / IPS
7. Saving a record of sessions
8. Sending logs to SIEM / Syslog
Key features
- Provides protection of access to servers (Windows, Unix, Linux, Mainframe), databases, network devices and other infrastructure devices using administration protocols;
- Control of widely used administration protocols SSH, RDP, HTTP/HTTPS, Telnet, etc.;
- Recording of work sessions of privileged users (system administrators, network engineers, senior staff of IT departments, outsourcing providers, etc.) using various protocols for later viewing and downloading videos;
- Creation and storage of all user activity logs (time, access subject and object, action on access object), providing a full reproduction of user actions with servers or information systems;
- Indexing video recordings and action logs, building a unified events base;
- Full-text search in the database, provision of various reports for each user, distribution of reports to interested parties, including scheduled;
- Support for the installation of a significant number of collectors;
- Zonal or centralized audit execution (for the entire infrastructure);
- Integration with modern SIEM (security information and event management), IPS (intrusion prevention), Web filters, DLP (data leak prevention) systems, etc.
Key benefits
- Simple, flexible and efficient control over user actions, control of access to applications and functions performed on servers, provision of logs and video recordings of monitored events;
- Wide range of options for access settings for privileged users for almost any scenario: on schedule or on demand, for one or more times, by groups of available assets, etc. (granular access);
- Full control over the work of administrators and users with extended rights, including the ability to break the session in real time when spotting suspicious privileged users activity;
- Using the most efficient data recording and storage algorithms:
- Assignment of special timestamps to all data, allowing for quick search and ensuring the reliability of information;
- Reliable database protection (data is encrypted and stored independently with secure access to read and add new records);
- Extremely compact record size (up to 5 MB/h for indexed SSH sessions, up to 20 MB/h for RDP sessions with 1920x1080 resolution).
- Flexible methods of integration into the company's infrastructure:
- In a distributed infrastructure;
- “Into the gap” of the corporate IT system;
- In various modes:
- Bastion, proxy mode—servers for connections;
- L3—router mode (privileged users and target servers are on different networks);
- L2—network bridge mode (processing of all traffic, including VLAN).
- Reduced deployment and maintenance costs—SafeInspect does not require installation of agent software on administered devices or workstations;
- Installation both on hardware (server) and in a virtual environment: VMware, Hyper-V, Virtualbox;
- Quick system deployment:
- Up to 20 minutes for the main delivery option—Virtual Appliance;
- ~ 2 hours—deployment with settings for full operation.
- Minimal intervention in the network infrastructure;
- Increasing the level of security: the use of two-factor authentication using tokens (for example, E-token, Rutoken), as well as a one-time password system;
- Fault tolerance, work both in autonomous and distributed mode, high availability of the system;
- An import-independent solution that covers all the necessary requirements of regulators:
- Federal Law No. 152 (On personal data);
- Federal Law No. 187 (On the security of the critical information infrastructure of the Russian Federation);
- Order of FSTEC No. 239 (Safety measures for significant critical information infrastructure facilities);
- GDPR (European data protection regulation).
- The product is included in the Unified Register of Russian Computer Programs and Databases;
- Availability of Russian FSTEC and FSB certificates;
- Application to control data security in any government information systems.
Branch
Platform